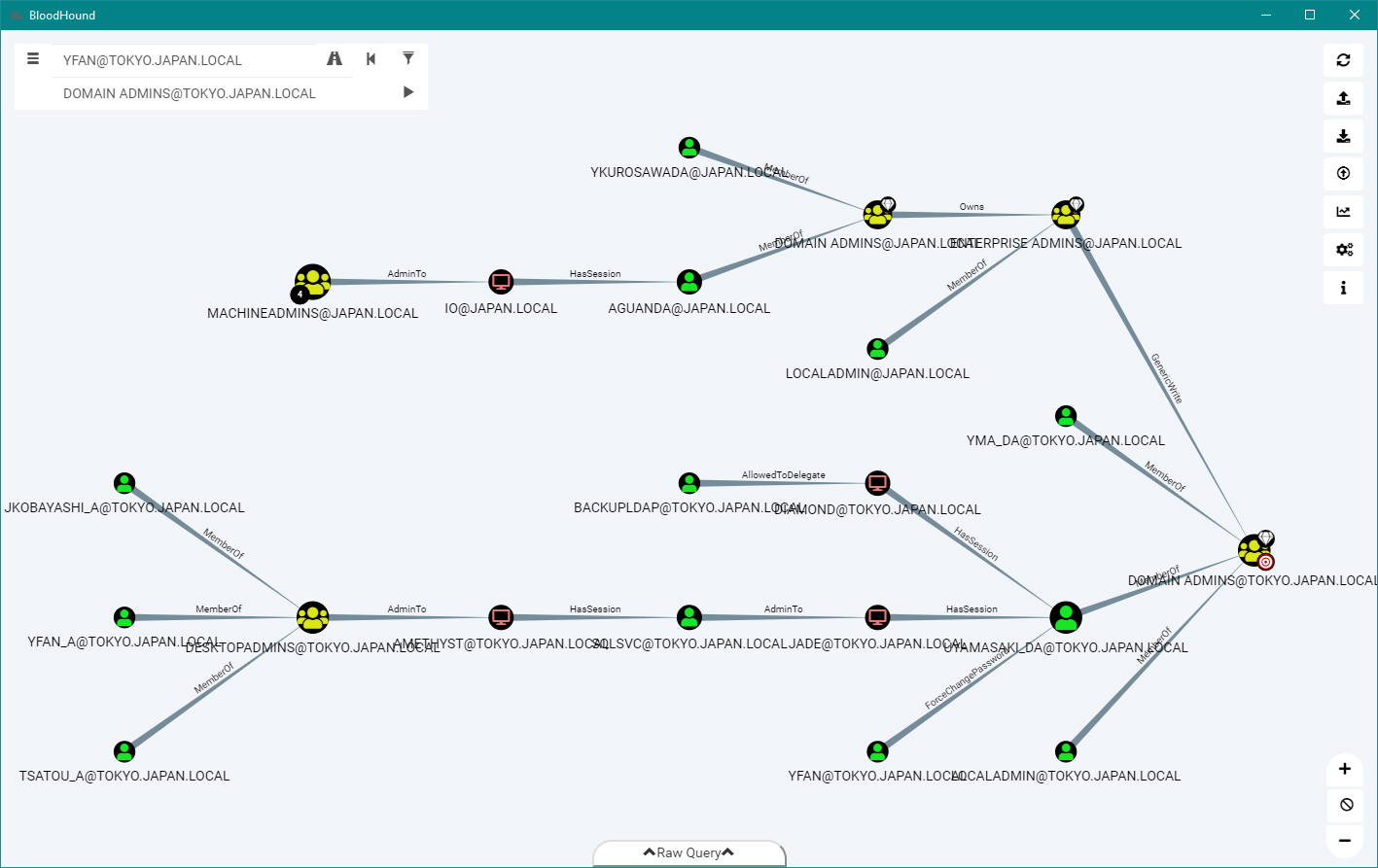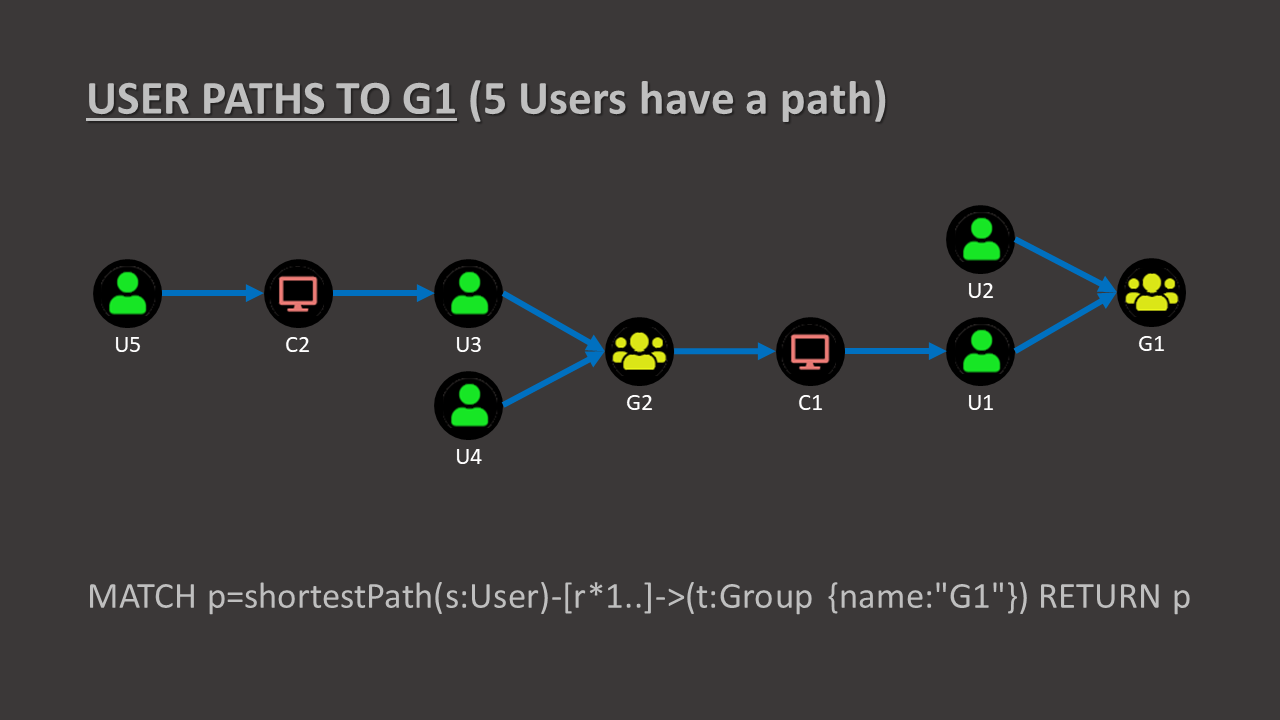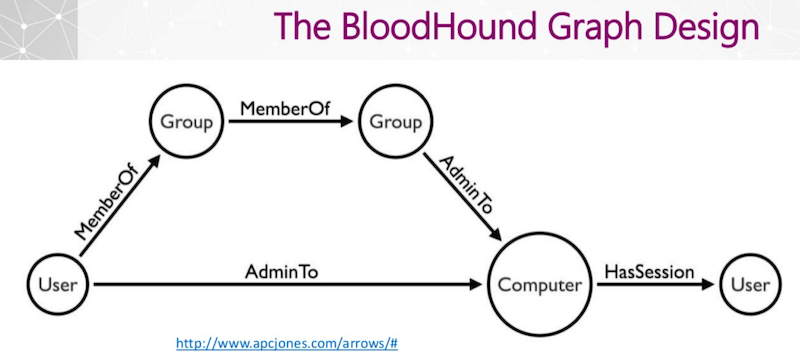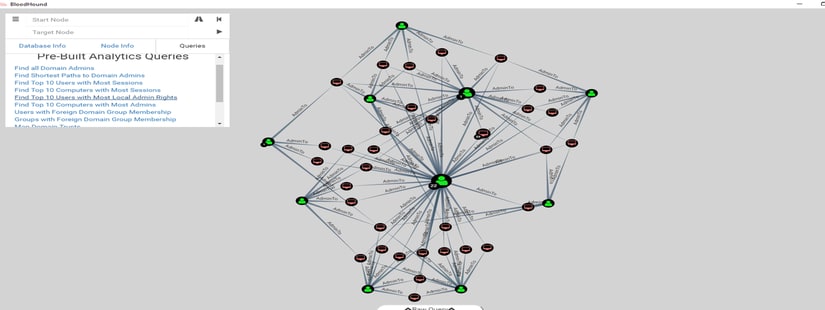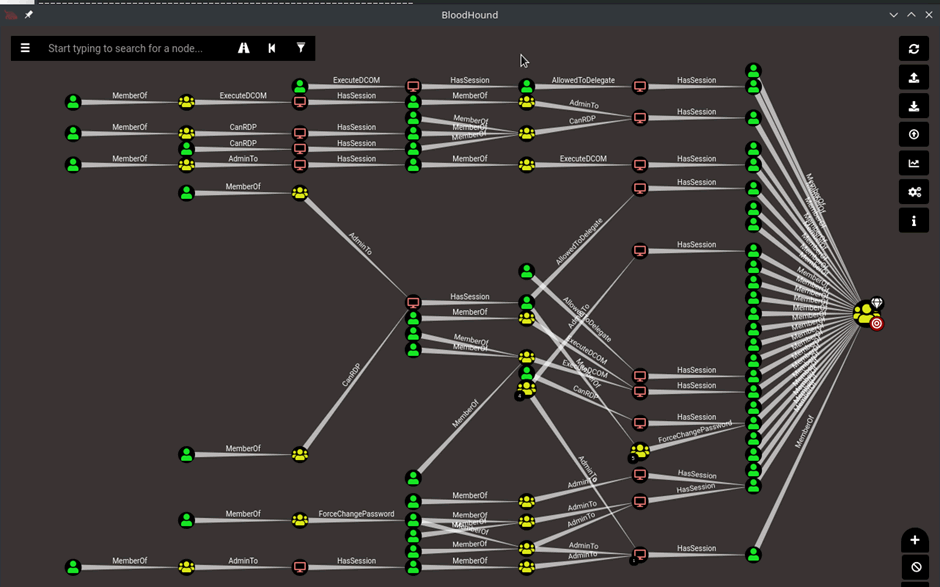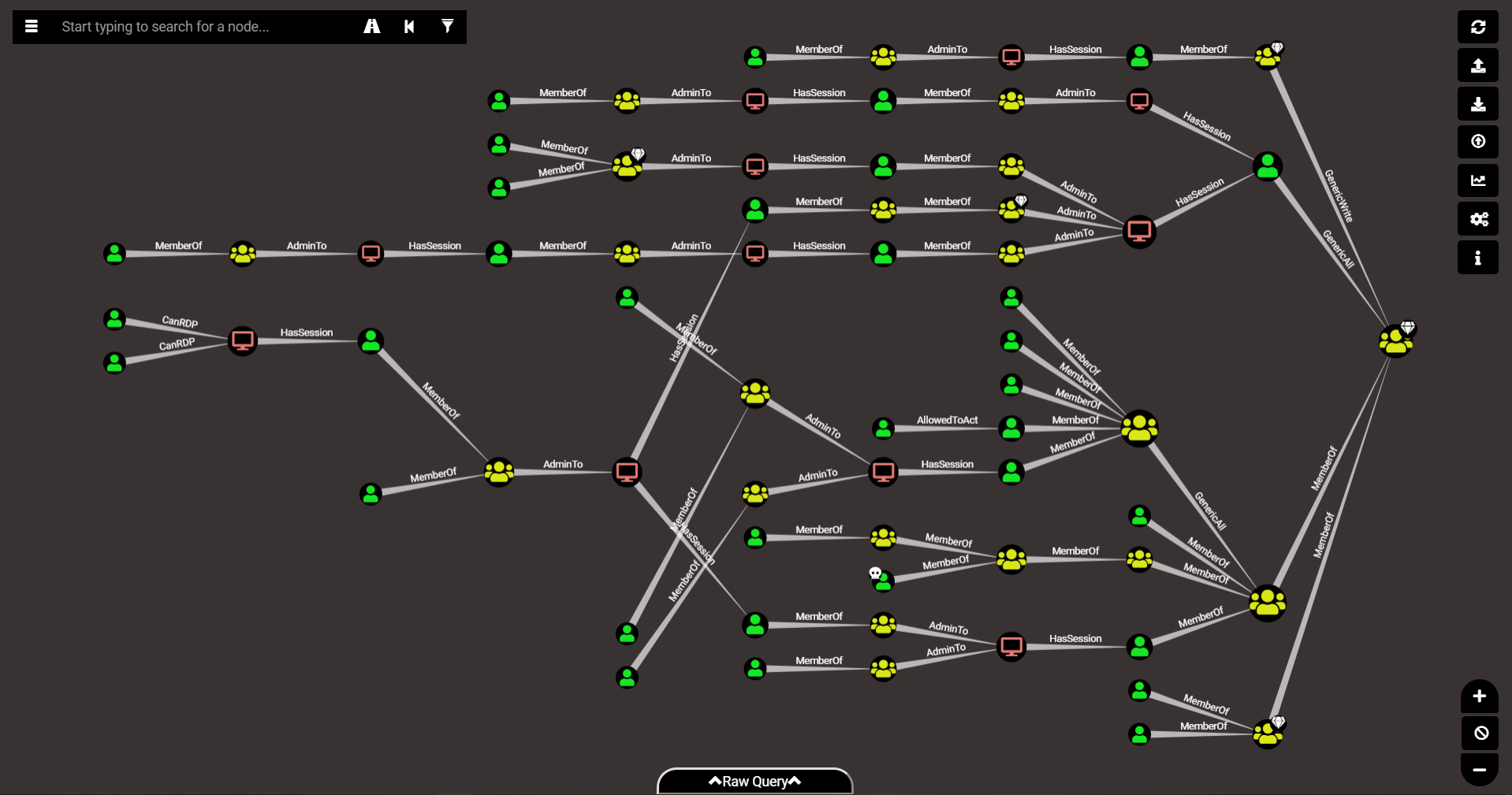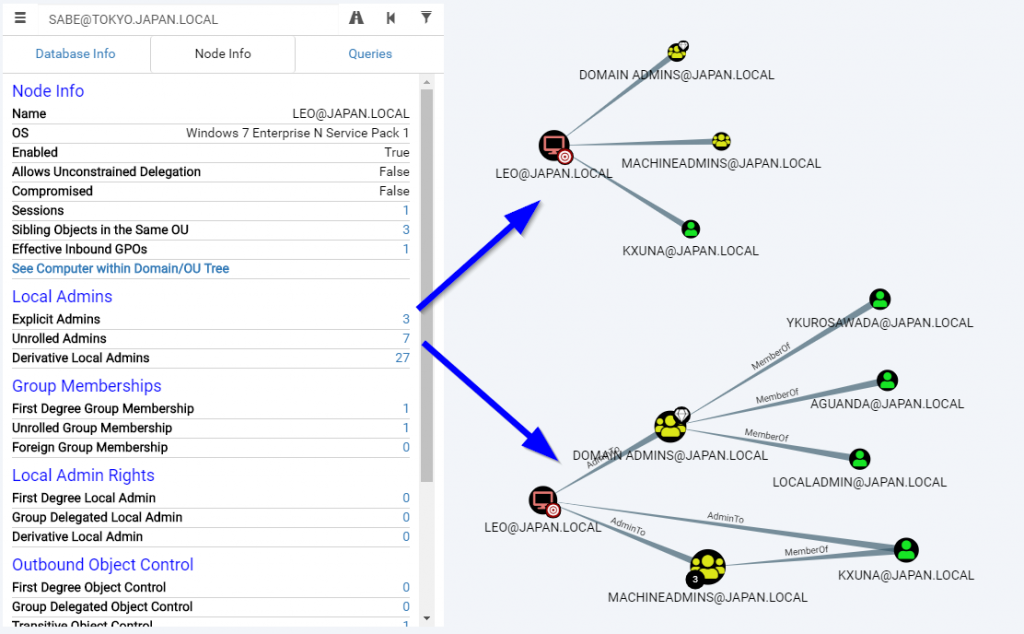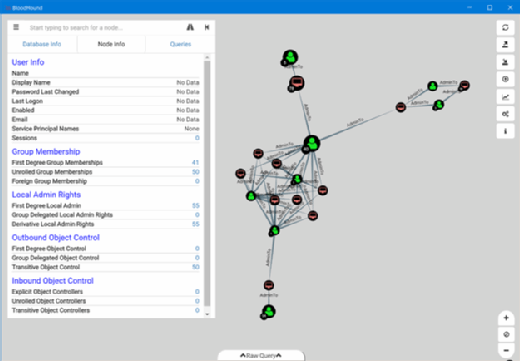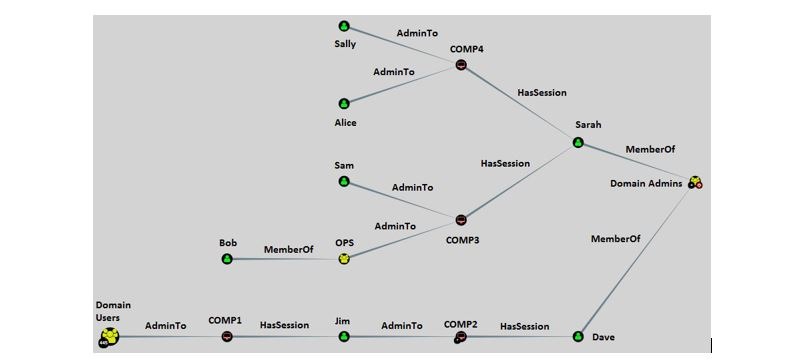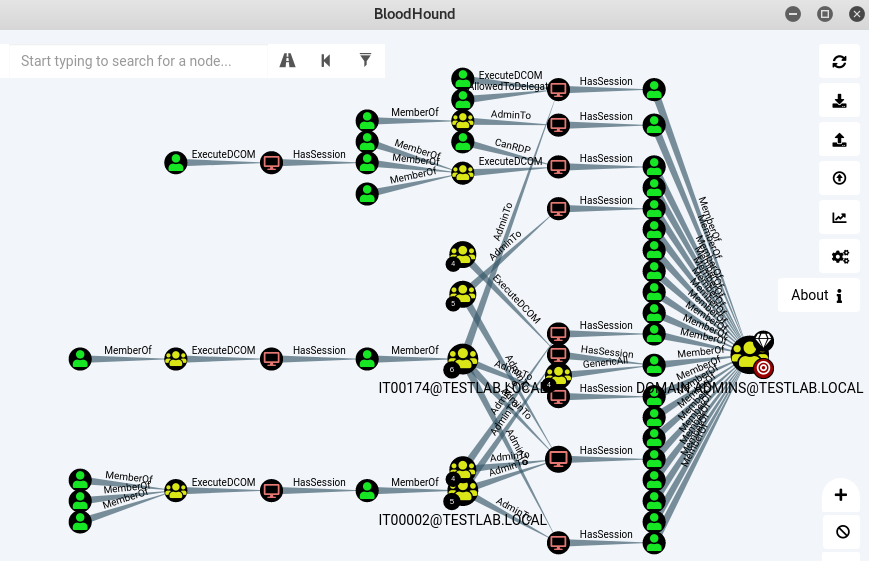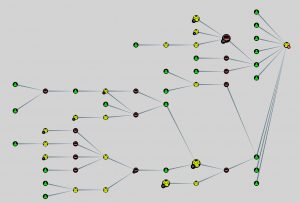
Bloodhound – A Tool For Exploring Active Directory Domain Security - Latest Hacking News | Cyber Security News, Hacking Tools and Penetration Testing Courses

SpecterOps BloodHound Enterprise enables organizations to eliminate critical AD attack paths - Help Net Security